What Is DKIM? Email Authentication Methods Made Easy

DKIM is an essential component of a complete email security program. It not only protects the sender from falling victim to email spoofing, and thus being unknowingly complicit in spam and phishing mail, but also is a key part in establishing trust between an email server and ISPs. This trust has a huge impact on the deliverability of the emails sent from an email server, so using DKIM makes it much more likely your emails don’t get marked as spam.
For anyone who doesn’t work in internet security, or is still inexperienced, this article should serve as a guide to help you get up to speed with DKIM, as well as to understand its relationship with SPF and DMARC, two more essential parts of email security.
What is DKIM (DomainKeys Identified Mail)?

First things first. DKIM (DomainKeys Identified Mail) is a standard authentication protocol used in email communications to verify that emails were genuinely sent from the stated address and domain, and have not been manipulated during the transmission.
How does DKIM work?
DKIM is basically used to prove the identity of senders: it works by giving the sent email a unique signature, usually placed in the header of the email, or in the body of the text. This DKIM signature is then checked by the receiving SMTP server to determine if the email was indeed sent by the domain it claims to have been sent by.
DKIM can be confusing and a little overwhelming for people who don’t work in IT or other tech fields. But it doesn’t have to be. Here’s a simplified breakdown of just how DKIM works from start to finish:
1. An email is sent with a DKIM signature (generally in the header of the email).
2. The email arrives at the intended destination. With a pair of keys – one public key, one private key.
3. The email receiver (e.g. Gmail, Outlook, etc) checks the DKIM signature in the email.
4. The email receiver then runs a DNS query (Domain Name System – basically, a phonebook for internet domains). This query lets the receiver find the key to decrypting the DKIM signature – the public key – which is then used to verify the unique DKIM signature – the private key.
5. Once decrypted, the email receiver can read the “hash value” of the email – a long string of text which is only legible by computers.
6. This hash value is then checked against the original hash value (created when the email was first sent).
7. If the hash value of the received email matches the original hash value (meaning the message was unchanged and sent by the original domain), then the DKIM is passed.
Don’t worry, to make things clearer we’ve also created this infographic. You’re welcome ?.

But, this is assuming that all goes well.
In the case that the receiving email server fails to check and validate the DKIM signature, it sometimes spells bad news for the sending server. The most common consequence is that the message gets marked as spam – meaning the recipient never reads your message. At worst, the entire IP address of the sending server could be blocked.
What are the benefits of DKIM?
Whether you have a single, personal email address or if you manage the email server of an entire organization, employing DKIM to your email server is clearly beneficial, as are all additional layers of digital security.

Benefit 1: Appear legitimate, avoid the spam folder
Even though the algorithms being used to detect spam are incredibly sophisticated, very often spam slips past the filter and still land in inboxes, while one in six authentic emails will never reach the inbox.
This can mean a death sentence for email marketing campaigns and other communications. DKIM helps email senders avoid these false-positive results. DKIM gives a clear legitimacy to your email recipients and, more importantly, to their email server. The chance of being marked as spam or junk falls dramatically with DKIM’s extra layer of legitimacy.
As a result of implementing the DKIM protocol, email deliverability should significantly improve. So, the more you send genuine emails to people, and the more these emails use other best practices for deliverability rates, the more likely your domain will remain in good standing with ISPs (Internet Service Providers).
Benefit 2: Protect against malicious emails
On the other side of the coin, DKIM is a valuable feature to include on your own email server. The main benefit of doing this is to help better filter out unwanted incoming emails and protect yourself and your entire organization from harmful incoming communications
Be they simple, unwanted spam messages, to which the recipient has not consented, or at worst, fake emails or phishing schemes – emails disguised as having been sent from the user of the email account, but really contain malicious, data-stealing links and attachments, added by bad-acting third parties.
How is DKIM related to SPF and DMARC?
If you hear the words SPF and DMARC when talking about DKIM, don’t panic.
There is a whole lot of overlap within these three authentication protocols. This is true both of how these systems work on a technical level, and also how they are applied within email security.
What is SPF?
Sender Policy Framework or SPF detects fraudulent and spam emails by checking that they have been sent by an authorized host from the stated domain.
It does this by checking the DNS TXT records for the domain from which the email is sent to see if it has come from an authorized host. SPF checks the IP address of this host during the delivery of the email. If the host isn’t on the list of authorized IP addresses, then it is flagged as a likely fraudulent email.
What is DMARC?
DMARC, or Domain-based Message Authentication, Reporting, and Conformance, is an email authentication protocol built on the policies established by SPF and DKIM. Thanks to DMARC, domain owners can tell ISPs how to deal with incoming emails under their domain and what to do in case they fail SPF or DKIM authentication.
However, strong DMARC policies can sometimes misidentify legitimate emails as fraudulent when delivered via a third party such as eEvidence. When this happens, your emails get bounced back to you with an error that looks like this one: “550-5.7.1. Unauthenticated email from yahoo.com is not accepted due to domains 550-5.6.1 DMARC policy”.
That said, DMARC shouldn’t be considered a replacement for both systems – the best practice for full security is to employ all 3 options together.
Similarities and differences between DKIM, SPF, and DMARC
As a final breakdown, let’s take a quick look at the similarities between DKIM, SPF, and DMARC, as well as the ways in which they differ.
Similarities
- DKIM, SPF, and DMARC are systems of email authentication
- All 3 are used to protect email senders from being used as email spoofing by online bad actors
- They also all protect incoming email servers by more accurately detecting and filtering out untrustworthy emails
- Each of these systems relies on DNS entries for authentication
Differences
- DKIM is primarily a method of validating whether or not the contents of an email have been unaltered and are trustworthy, whereas SPF checks whether or not the sending server is allowed to send from the given domain. DMARC boosts the effectiveness of SPF and DKIM both by establishing a clear policy for them both.
- While DKIM and SPF have been adopted quite widely, DMARC is still lagging, especially in certain industries such as non-profits.
Should I use DKIM when I send emails?
The short answer here is an emphatic yes.
Without DKIM, if a bad-acting third party gains access to your email server, then they could have free rein to send out malicious emails that pretend to come from a trustworthy source.
The slightly longer answer would be: yes, in conjunction with SPF and DMARC. For the reasons listed above, the most secure strategy, and the one that should be employed by all organizations, is to use DKIM, SPF, and DMARC together.
Can I have my emails certified if I have DKIM in place?
Besides sending emails that are verified as authentic by using DKIM, SPF, and DMARC, can you also get them legally certified as having been sent and delivered to the recipient?
Yes, of course. Registered email is what you are looking for. This type of email adds an extra layer of verification to outbound emails, meaning the email is not only much more likely to pass spam and junk filters, but as the sender you’ll get legal evidence of your email with proof of delivery. This is a transparent process that doesn’t require the intervention of the recipient. The email is delivered in a few seconds just like a normal email, but this time you’ll have legal evidence of its contents and delivery.
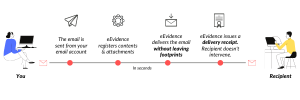
Certifying an email works in tandem with authentication protocols and gives you full peace of mind, especially when handling important communications that you’re interested in keeping proof of. All you need to do is update your DNS records to validate and “authorize” that the emails you send are delivered by eEvidence.
We hope you found this post useful and we encourage you to try our registered email service. You only need to set up your account and start registering the emails you send by using any of the methods available. It’s easy, fast, reliable, and cost-effective. You can even try it for free… ?
If you are interested in starting to to communicate with greater guarantees and you are a professional, particular and/or small company, do not hesitate to consult the different rates available and register. If on the other hand, you are a company with high volumes of shipments and needs tailored to your project, please contact us.



